In this post, we will be going over the Stuxnet virus using Volatility.
Pre-Start
A reoccurring piece of information that is needed for this investigation is the image profile. This is done by using the imageinfo command.
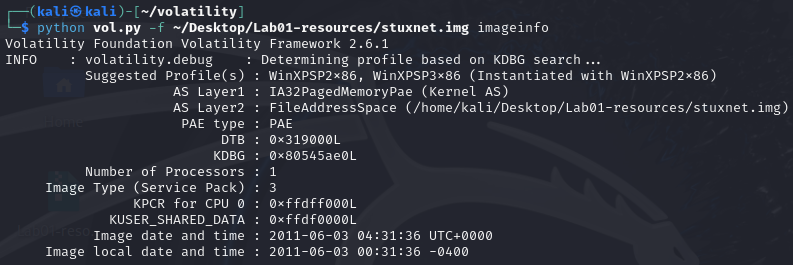
The suggested profile is WinXPSP2x86.
Part I - Services/Processes
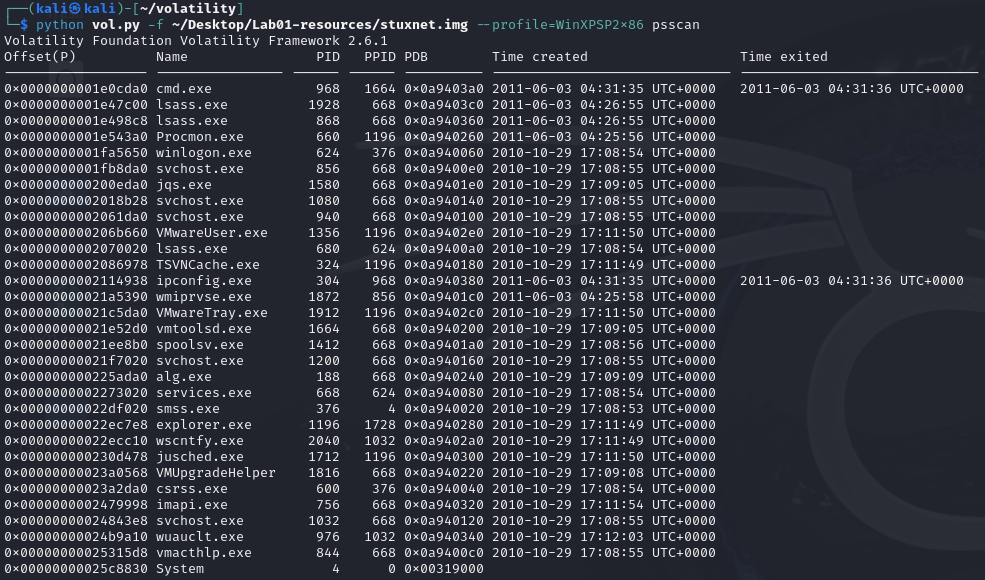
First section is the most basic. Using the psscan and pstree commands we can find the active running processes on the machine.
In this process tree, the red outlined processes seem to be normal (winlogon.exe is the parent of the red lsass.exe). The purple outlined processes are the suspicious ones. The lsass.exe copies in purple have the parent of the services.exe.
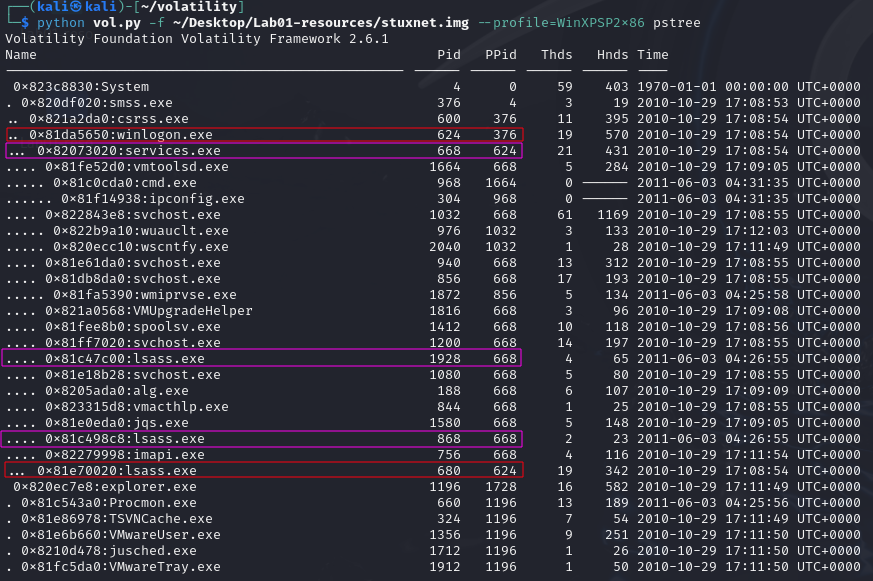
Looking at these processes the only thing that sticks out is the multiple instances of the lsass.exe. After some research, lsass.exe is the Local Security Authority Subsystem Service. This service is a core service and its only parent should be either winlogon.exe or in Vista and later, it is created by the wininit.exe.$^{[1]}$
This diagram contains the inner workings of the Local Security Authority Subsystem Service. This could be dated after XP but this is generally how it works.
.gif)
So we have identified that two suspicious processes through pstree. Both are children of PID 668.
lsass.exe: PID: 868lsass.exe: PID: 1928
Part II - Process Hashes
Most detected viruses are detected through hash matches, using VirusTotal we can check the hash of a given process and figure out if it is malicious.
To dump the processes and take a look into the hashes we can use the procdump command.
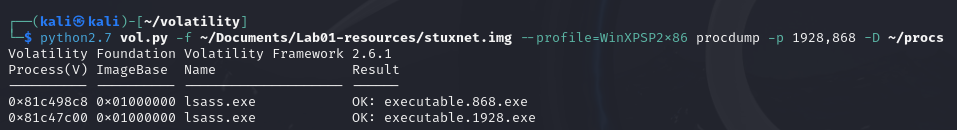
Then we can check the sha256 hashes using sha256sum.
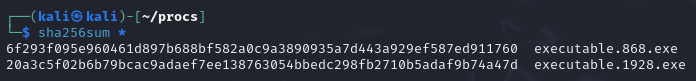
Now we can take a look at these two processes hashes on VirusTotal and see if they are malicious.
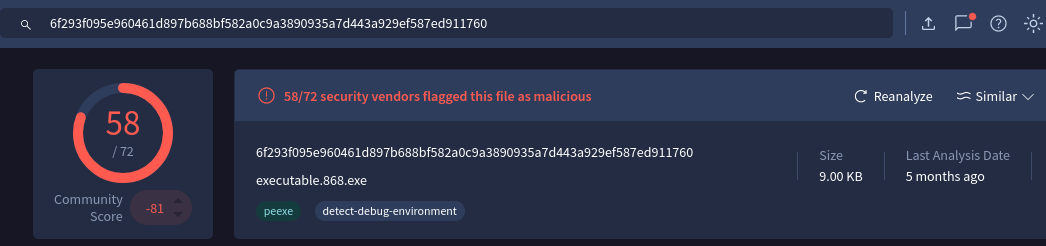
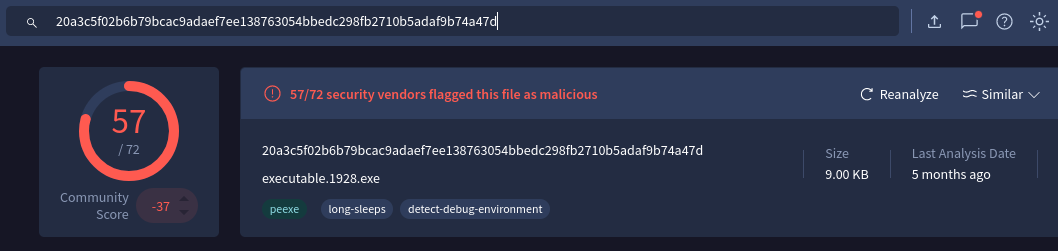
References
| 1 | Mark Russinovich: Analyzing the Stuxnet Virus with Sysinternals Tools (Part 1) |
| 2 | Mark Russinovich: Analyzing the Stuxnet Virus with Sysinternals Tools (Part 2) |
| 3 | Mark Russinovich: Analyzing the Stuxnet Virus with Sysinternals Tools (Part 3) |
| 4 | MNIN Security Blog - Coding, Reversing, Exploiting (Stuxnet’s Footprint in Memory with Volatility 2.0) |
| 5 | Local Security Authority Subsystem Service - Wikipedia |